mikrotik
CHR
free/trial: https://help.mikrotik.com/docs/spaces/ROS/pages/18350234/Cloud+Hosted+Router+CHR#CloudHostedRouter%2CCHR-Freelicenses
download: https://mikrotik.com/client/chr
/system license renew level: p1
IPv6
Server: only delegate IPv6 prefixes, not addresses: https://wiki.mikrotik.com/wiki/Manual:IPv6/DHCP_Server
Performance
Hardware offloading(Chip) > Fast Forward(CPU) > Fast Path > Slow Path
Tasks
if winbox not working:
/webfig/#IP:Servicescreate/dump/unpack .npk: https://github.com/kost/mikrotik-npk
vulnerabilities: https://github.com/microsoft/routeros-scanner
Monitor/control from Home Assistant: https://github.com/tomaae/homeassistant-mikrotik_router
Quickset
CPE: Client device
BasicAP: Wireless
HomeAP: Wireless/Guest; WAN; LAN; VPN; System update/reset/password
Wireless ISP (WISP) AP: 802.11/nstreme/nv2 Wireless Bridge/Router; VPN; System update/reset/password
Home Mesh: Enables the CAPsMAN server in the router, and places the local WiFi interfaces under CAPsMAN control. Just boot other MikroTik WiFi APs with the reset button pressed.
not adding self => Wireless -> CAP: CAPsMAN addr add "127.0.0.1"
"No supported channel" => reset with default config and run quickset first
PTP Bridge AP: transparently interconnect two remote locations together in the same network, set one device to this mode, and the other => PTP Bridge CPE
CPE
https://wiki.mikrotik.com/wiki/Manual:Wireless_Station_Modes#Mode_station-pseudobridge
802.11
station: if L2 bridging on station is not necessary - as in case of routed or MPLS switched network
station-pseudobridge : single MAC address translation
station-pseudobridge-clone : either address configured or first forwarded frame
Wireless
RouterOS AP accepts clients in station-bridge mode when enabled using bridge-mode parameter.
default-forwarding (on AP) – gives ability to disable the communication between the wireless clients default-authentication – enables AP to register a client even if it is not in access list. In turn for client it allows to associate with AP not listed in client's connect list
Reset
https://help.mikrotik.com/docs/display/ROS/Reset+Button
Hold this button before applying power
three seconds : backup boot loader
flashing : reset configuration
5 more seconds, LED turns solid : CAP
5 more seconds until the LED turns off : Netinstall
QoS
https://help.mikrotik.com/docs/display/ROS/Connection+rate
PCQ
https://wiki.mikrotik.com/wiki/Manual:Queue_Size http://mum.mikrotik.com/presentations/US08/janism.pdf https://wiki.mikrotik.com/wiki/Manual:HTB-Token_Bucket_Algorithm
Cake
https://help.mikrotik.com/docs/display/ROS/CAKE
config example: https://forum.mikrotik.com/viewtopic.php?t=188420#p1051514
https://help.mikrotik.com/docs/spaces/ROS/pages/196345874/CAKE
ack-filter: improve the utilization of the upload bandwidth
diffserv8 : 5. Real-time Interactive (40): Interactive applications, such as gaming.
hotspot
Routing
Packet Flow
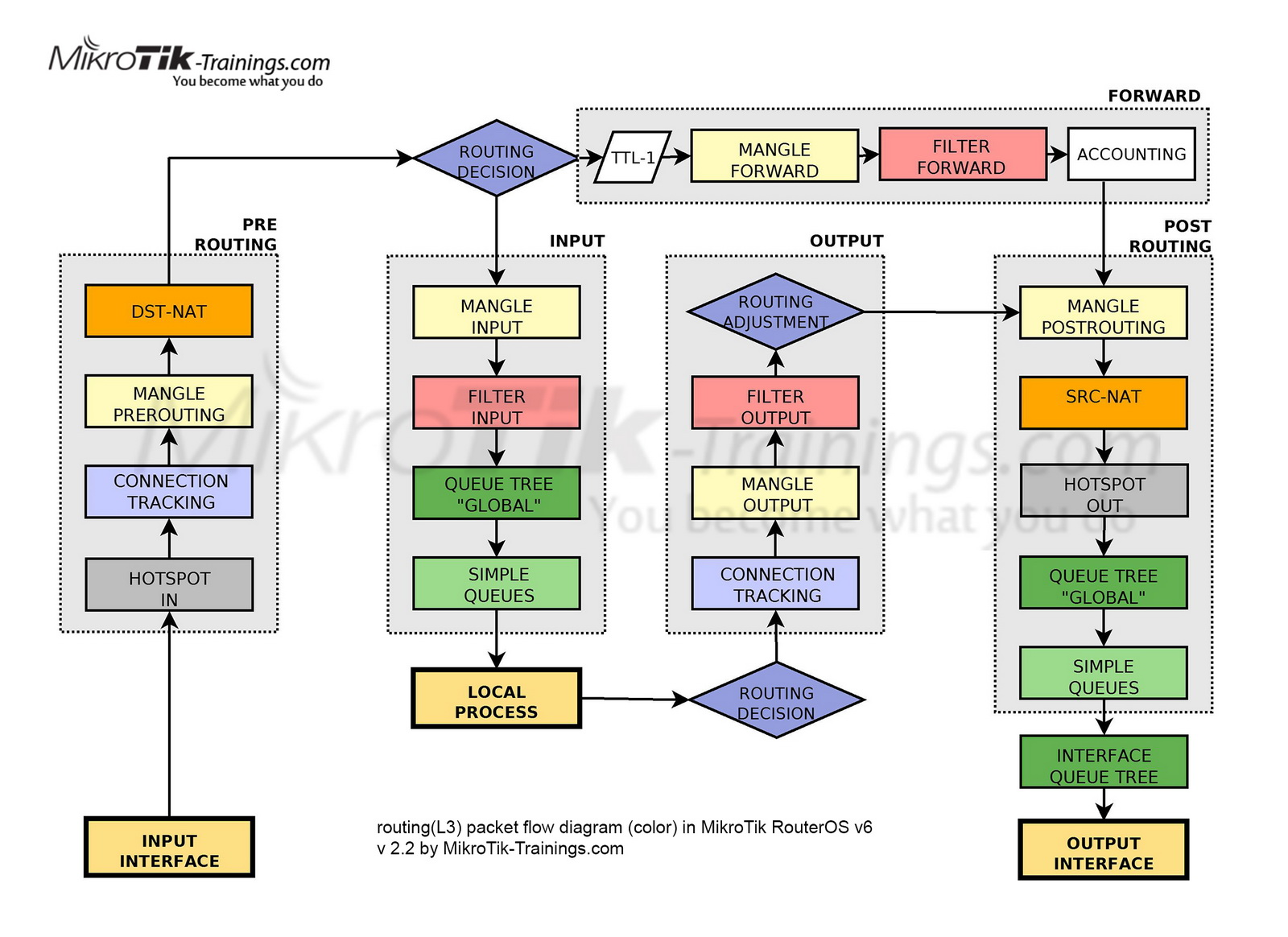
Models
Switch Chip
https://wiki.mikrotik.com/wiki/Manual:Switch_Chip_Features
Feature
QCA8337
Atheros8327
Atheros8316
Atheros8227
Atheros7240
MT7621
Port Switching
yes
yes
yes
yes
yes
yes
Port Mirroring
yes
yes
yes
yes
yes
yes
TX limit
yes
yes
yes
yes
yes
no
RX limit
yes
yes
no
no
no
no
Vlan table
4096 entries
4096 entries
4096 entries
4096 entries
16 entries
no
Rule table
92 rules
92 rules
32 rules
no
no
no
Switch VLAN
vlan-mode # QCA8337(RB3011) and Atheros8327(RB951G-2HnD): when vlan-mode=secure is used, it ignores switch port vlan-header options.
fallback
check ingress
If ingress traffic is tagged and egress port is not found in the VLAN table for the appropriate VLAN ID, then traffic is dropped.
forwards all untagged traffic. If a VLAN ID is not found in the VLAN Table, then traffic is forwarded. Used to allow known VLANs only in specific ports.
check
check ingress, drops all untagged traffic.
If ingress traffic is tagged and egress port is not found in the VLAN table for the appropriate VLAN ID, then traffic is dropped.
secure
check ingress, drops all untagged traffic. Both ingress and egress port must be found in the VLAN Table for the appropriate VLAN ID, otherwise traffic is dropped.
vlan-header
=leave-as-is default
=always-strip for access ports
=add-if-missing for trunk port
Bridge VLAN
way 1: add br-vlan: if-vlan + phy-access-port
way 2: set filtering: https://wiki.mikrotik.com/wiki/Manual:Interface/Bridge#Bridge_VLAN_Filtering
FastPath + Conntrack = FastTrack
https://mum.mikrotik.com/presentations/UA15/presentation_3077_1449654925.pdf
https://mum.mikrotik.com/presentations/TR18/presentation_5628_1539936230.pdf
https://wiki.mikrotik.com/wiki/Manual:Fast_Path
https://wiki.mikrotik.com/wiki/Manual:IP/Fasttrack
Sniffer and Wireshark
https://mum.mikrotik.com/presentations/ID19/presentation_6708_1572241150.pdf
VPN
OpenVPN
https://wiki.mikrotik.com/wiki/OpenVPN
tun, RouterOS defines this as ip. tap, which is needed for bridge mode gateways. RouterOS defines this as ethernet.
WireGuard
Both WAN: https://help.mikrotik.com/docs/display/ROS/WireGuard 1 Server: https://forum.mikrotik.com/viewtopic.php?t=174417
PPP BCP
https://wiki.mikrotik.com/wiki/Manual:BCP_bridging_(PPP_tunnel_bridging)
mwan
Bandwidth-based load-balancing with failover: https://mum.mikrotik.com/presentations/US12/tomas.pdf
Bonding: - You need to control of both ends of the link Policy routing: - Not dynamic / Scalability problems PCC: - Not bandwidth wise Bandwidth based: + scalable | MPLS TE / Mangle + scripting
Bandwidth based - Mangle + scripting
Steps: from page 23
PCC - diff subnet/bandwidth
https://mum.mikrotik.com/presentations/US12/steve.pdf mark connections -> associate routing marks with packets -> Create routes
p81: action=accept chain=prerouting dst-address=172.*.0.0/24
p91: action=mark-connection chain=prerouting connection-mark=no-mark in-interface=LAN new-connection-mark=WAN1 passthrough=yes per-connection-classifier=
p100a: action=mark-routing chain=prerouting connection-mark=WAN1 new-routing-mark=WAN1-mark passthrough=yes
p100b: action=mark-routing chain=output connection-mark=WAN1 new-routing-mark=WAN1-mark passthrough=yes
p104: action=mark-connection chain=prerouting connection-mark=no-mark in-interface=WAN1 new-connection-mark=WAN1 passthrough=yes
https://aacable.wordpress.com/2011/07/27/mikrotik-dual-wan-load-balancing-using-pcc-method-complete-script-by-zaib/
WAN + ppp
Videos
TopCommon mistakes: https://www.youtube.com/watch?v=3LmQYIQ5RoA
Automation
Web Helper | need SignUp: https://github.com/buananetpbun/buananetpbun.github.io | https://buananetpbun.github.io/
Scripting
https://wiki.mikrotik.com/wiki/Manual:Scripting
https://github.com/eworm-de/routeros-scripts
SSH
https://help.mikrotik.com/docs/display/ROS/SSH
API
https://help.mikrotik.com/docs/display/ROS/API#API-Exampleclient
Python
https://github.com/LaiArturs/RouterOS_API
https://librouteros.readthedocs.io/en/latest/query.html
Monitoring
Grafana & Prometheus
Py + Dockerfile : https://github.com/akpw/mktxp
Grafana | docker-compose : https://github.com/akpw/mktxp-stack
Grafana | RouterOS v7 + Raspi: https://github.com/M0r13n/mikrotik_monitoring
docker exec -it mktxp /bin/sh mktxp show # cat /root/mktxp/mktxp.conf mktxp print -en 'Sample-Router' -cc # test connection & show CAPsMAN clients
Go + Dockerfile: https://github.com/nshttpd/mikrotik-exporter
Grafana | k8s: https://www.lisenet.com/2021/monitor-mikrotik-router-with-grafana-and-prometheus-mikrotik-exporter/
Manage Remote
ROS v7: conf socks4 and route
Wireless
802.11r/k/v
7.13+ | https://help.mikrotik.com/docs/display/ROS/WiFi#WiFi-Compatibility
for ARM | NOT copmatible: MIPS
Last updated